Originally published in Inside GNSS (May/June 2025). Read the full piece there.
Spoofing is no longer a niche concern—it’s a growing threat to GNSS-reliant systems across aviation, autonomy, and logistics. This article explains how Swift’s SkylarkTM GNSS correction service defends against spoofing through secure infrastructure, anomaly detection, and validated satellite data.
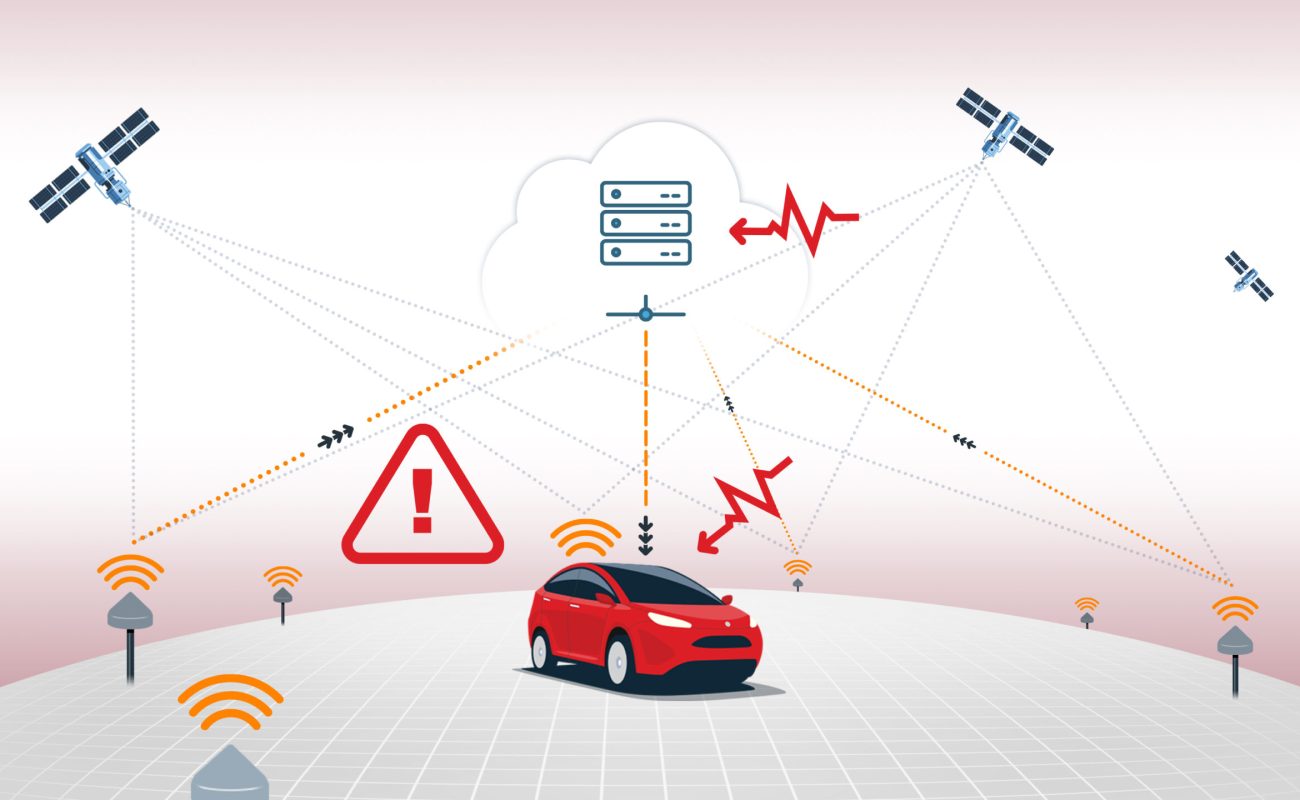
Global Navigation Satellite Systems (GNSS) are the unseen backbone of our modern world, underpinning everything from precise agricultural applications to autonomous vehicle navigation. Yet, a growing and insidious threat looms: GNSS spoofing. This technique, where attackers deliberately manipulate positioning data, is no longer a theoretical concern. With the proliferation of low-cost tools and escalating geopolitical conflicts, spoofing incidents are on the rise, impacting critical infrastructure and everyday operations.
The consequences extend far beyond military targets. Commercial aviation, maritime navigation, and ground-based systems like autonomous vehicles and industrial robots are all vulnerable. Recent events in Ukraine and the Middle East have highlighted the severe disruptions spoofing can cause, forcing pilots to resort to alternative navigation and raising serious safety concerns.
To truly grasp the challenge, we need to understand the various ways attackers can mislead GNSS receivers. Our latest contributed article for Inside GNSS breaks down four major categories of spoofing attacks and, crucially, how Swift Navigation’s Skylark Precise Positioning Service provides robust defenses.
Tap or hover to reveal how Swift detects and defeats spoofing attacks.

The Four Faces of GNSS Spoofing and How Swift Fights Back
1. RF Spoofing at Receivers: Directly Attacking User Devices
The Attack: This is the most common form, involving broadcasting counterfeit GNSS signals to overpower real satellite transmissions.
Attackers can either replay genuine signals (meaconing) or generate entirely new, artificial ones that precisely mimic satellite motion and data, leading a receiver to compute an incorrect position or time. The challenge for attackers increases with multi-frequency, multi-constellation receivers.
Swift’s Defense: Swift’s solutions employ multiple layers of protection. Authenticated Ephemeris allows receivers, powered by services like Skylark, to detect mismatches between verified satellite data and spoofed signals. Sensor Fusion, using Swift Navigation’s Starling Positioning Engine, cross-references GNSS data with IMU and odometry readings, identifying inconsistencies that signal a spoofing event and enabling the system to switch to dead reckoning. Furthermore, leveraging Multi-Constellation Protection makes it exponentially harder for attackers to spoof all signals simultaneously.
2. RF Spoofing at CORS: Compromising Reference Stations
The Attack: Instead of targeting individual devices, attackers could spoof Continuously Operating Reference Stations (CORS) used in high-accuracy correction services like RTK.
This could lead to widespread distribution of erroneous corrections, impacting entire industries such as autonomous navigation, land surveying, and precision agriculture. While large position shifts at a fixed CORS are easily detected, subtle manipulations of satellite ephemerides and clock data—without changing the station’s reported position—are far more difficult to identify and can propagate critical errors.
Swift’s Defense: Skylark employs sophisticated safeguards for its reference station network. Position Anomaly Detection flags even subtle deviations in a CORS’s reported position. An Ephemeris Voting Mechanism cross-validates ephemerides across the entire network, rejecting outliers. In the event of a compromise, Automated Station Quarantine immediately isolates the affected CORS, ensuring the integrity of the correction model. Continuous Clock Monitoring also tracks GNSS clock biases in real time, triggering quarantine for unexpected deviations.
3. Correction Data Tampering: Intercepting and Manipulating Correction Streams
The Attack: This cyber-attack-like method involves intercepting, modifying, or injecting false GNSS corrections before they reach a receiver, often over unsecured channels (e.g., unencrypted IP or open radio links).
Attackers can block corrections (denial-of-service), inject false data to subtly manipulate positioning, or even impersonate legitimate providers. This can introduce positioning errors without typical RF signal disruption, making it stealthier.
Swift’s Defense: Swift prioritizes data integrity and security. Encrypted Corrections prevent interception and modification. Authentication & Integrity Checks using digital signatures ensure corrections originate from a trusted source and remain unaltered. Tamper-Resistant Transport over secure, authenticated channels significantly reduces vulnerability to man-in-the-middle attacks. Critically, Fallback Mechanisms ensure that if corrections fail integrity checks, the receiver disregards them and switches to raw GNSS or dead reckoning.
4. Server Data Injection: Compromising Correction Processing Servers
The Attack: Here, attackers inject false GNSS observation data directly into the cloud servers responsible for computing corrections.
This network-based attack, distinct from RF spoofing, can lead to widespread distribution of erroneous data across a correction service’s user base, posing significant risks to industries reliant on high-precision positioning. Services with weak cloud security and data integrity measures are particularly vulnerable.
Swift’s Defense: Skylark leverages the robust security of its underlying infrastructure. Built on Secure Cloud Infrastructure (Amazon Web Services), Skylark benefits from AWS’s built-in encryption, identity management, and network security. Diversified Compute Environments (using both ARM-based and x86 AWS instances) reduce the risk of single-architecture vulnerabilities. Geographically Distributed Redundancy across AWS Availability Zones provides fault isolation, preventing localized disruptions. Furthermore, Skylark’s ISO 26262-Certified Safety ensures the service meets stringent automotive safety standards for security and reliability.
A Secure Path Forward
GNSS spoofing is a rapidly evolving threat demanding robust countermeasures. Swift Navigation’s Skylark Precise Positioning Service is a proven solution for mitigating these risks, delivering secure, high-accuracy GNSS corrections. By leveraging network-validated ephemeris, real-time anomaly detection, encrypted correction streams, and a robust cloud-based security architecture, Skylark ensures trusted GNSS data even in contested environments.
With variants optimized for different applications—from 1 cm to 1 meter precision—Skylark is trusted by leading automotive OEMs, robotics companies, and more, powering millions of ADAS-enabled and autonomous vehicles and devices worldwide.
For a deeper dive into the technical intricacies of these attacks and the comprehensive defense strategies, read the full article on Inside GNSS: