What is GPS Spoofing?
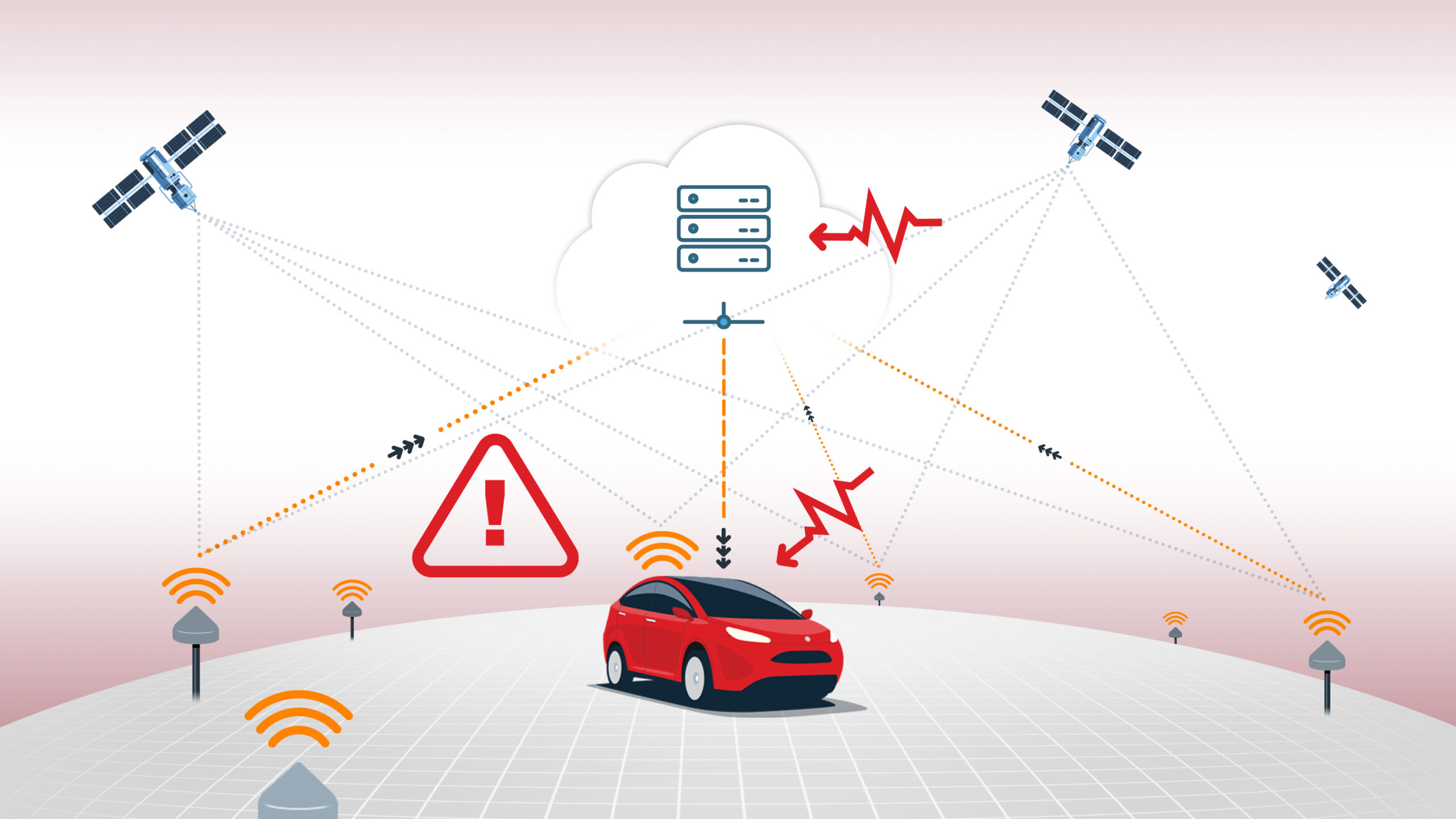
GPS/GNSS spoofing is a cybersecurity attack where malicious actors transmit fake GPS signals to deceive receivers into calculating incorrect position, navigation, or timing information. This sophisticated form of interference has evolved from a niche concern into a growing threat affecting GNSS-reliant systems across aviation, autonomy, defence, and logistics sectors.
Unlike jamming, which simply blocks or disrupts satellite signals, spoofing involves broadcasting counterfeit signals that mimic legitimate satellite transmissions. These false signals can cause receivers to report inaccurate locations, leading vehicles or systems to believe they are somewhere they are not. The attack can be particularly dangerous because the receiver may continue to operate normally while being fed completely false positioning data.
Types of Spoofing Attacks
- Signal Replay: Captures legitimate signals and re-broadcasts them with a delay.
- Progressive Attacks: A subtle method starting with a single spoofed satellite (often one not yet visible to the vehicle) to slowly drift the receiver’s position.
- Ephemeris Manipulation: Broadcasting false satellite orbital data (ephemerides) to force positioning engines to discard legitimate solutions.
Spoofing Detection & Mitigation Mechanisms
Modern receivers use internal monitors to identify inconsistencies in the radio frequency (RF) environment:
Autocorrelation Monitoring (ACM): This identifies signal distortion. In a spoofing attack, the interaction between the authentic and counterfeit signals creates a non-planar or “deformed” correlation peak.
False Lock Detection: Detection systems monitor signal characteristics to identify “mimic” signals. This typically requires a carrier-to-noise density ratio (C/N0) equal to or greater than 40 dB/Hz for a flag to be raised.
Early Frequency Ramp Identification: Identifies unnatural, sudden shifts in signal frequency that do not align with standard satellite orbital physics or vehicle motion.
Tracking Duration Requirements: To prevent a system from trusting a malicious signal immediately, satellites must be consistently tracked for at least 5 seconds before they are used in a position fix.
Industry Impact & Safety
The automotive industry has recognized spoofing as a critical safety concern, with leading manufacturers specifically requiring corrections services to implement anti-spoofing measures. These requirements include broadcasting corrections only for satellites visible in requested regions and implementing detection systems that can identify and mitigate progressive spoofing attacks.
How Swift Defends Against Spoofing
Skylark Precise Positioning Service defends against spoofing through a combination of secure infrastructure, advanced anomaly detection, and continuous monitoring of validated satellite data. By cross-referencing incoming signals against trusted reference stations, the system can identify discrepancies that indicate a malicious broadcast.
A core component of this defense is the Spoofed Queue mechanism. When the system detects suspicious signal characteristics, it moves the affected satellites into a dedicated “quarantine” queue for a configurable timeout period (typically 300 seconds by default). This prevents the potentially compromised data from influencing the navigation solution while the system continues to monitor the signal for legitimacy.
The system also utilizes a constellation-wide safeguarding protocol. If the number of compromised satellites from a single constellation exceeds a specific threshold (usually 5 satellites) the entire constellation is flagged as spoofed. This triggers immediate alarms and prompts the receiver to stop using that constellation entirely to maintain the integrity of the positioning fix.
Beyond these queueing protocols, Swift employs a multi-layered defense strategy. This includes the use of authenticated ephemeris to verify satellite orbital data and the Starling Positioning Engine, which uses sensor fusion to compare GNSS data against other vehicle sensors. By combining multi-constellation protection with these proprietary features, the system ensures a high level of resilience against both simple and sophisticated spoofing attempts.
Read our article to learn more: How Skylark Precise Positioning Service Defends Against GNSS Spoofing.
As GNSS systems become increasingly critical for autonomous vehicles, defence, and critical infrastructure, developing robust spoofing detection and mitigation capabilities remains essential for maintaining system integrity and safety.
Related Content
GNSS Basics

Devon Sharp

Marwan Ramadan

Marwan Ramadan

Devon Sharp

Devon Sharp

Marwan Ramadan

Devon Sharp

Marwan Ramadan
GIS

Devon Sharp

Devon Sharp
Robotics

Marwan Ramadan

Rai Gohalwar
Automotive

Devon Sharp

Marwan Ramadan

Joel Gibson

Marwan Ramadan